INTRODUÇÃO
Uma das peças mais sensíveis nas soluções fornecidas pela Prodist é o serviço de chaves privadas, que se enquadra aproximadamente em conceitos como o de cryptographic module (como em hardware cryptographic module, HSM) ou de key management system (KMS).
A ideia que une estes conceitos é a de isolamento de chaves privadas, ou seja, a ideia de um perímetro de segurança dentro do qual as chaves privadas estão encerradas, e para fora do qual elas nunca escapam.
O serviço de chaves privadas não fornece cópias das chaves privadas sob sua guarda, mas sim realiza operações criptográficas com essas chaves em nome da aplicação.
Em várias soluções fornecidas pela Prodist figura o Prodist STS acumulando inclusive a função de serviço de chaves privadas, projetado em 2002 para servir especificamente Mensagerias do novo Sistema de Pagamentos Brasileiro, e estendido em 2019 com capacidades suficientes para atender Mensagerias do recente Sistema de Pagamentos Instantâneos.
O programa servidor de chaves privadas, propriamente dito, o programa servidor STS, nasceu amarrado ao sistema operacional Microsoft Windows e permanece assim até hoje. Em 2024, a Prodist irá evoluir para o STS Multiplataforma, uma suíte de serviços básicos desamarrados de sistema operacional, homologados para produção em Microsoft Windows e Red Hat Enterprise Linux (ou equivalente).
COMPONENTES E SERVIÇOS
Para fornecer soluções multiplataforma, a Prodist projetou e está agora construindo as novas peças que fundamentarão a nova arquitetura, que grosso modo são três: o cofre de segredos, o serviço de chaves privadas e o serviço de certificados.
Cofre de segredos
Segredos em geral, e chaves privadas em particular, devem ter o seu acesso controlado com extremo cuidado para assegurar as propriedades de segurança que se pretende, como o não repúdio de assinaturas digitais. Soluções especializadas, como hardware security modules (HSM), oferecem níveis elevadíssimos de isolamento,
com propriedades como anti-tampering. Estas são, porém, soluções com alto custo de aquisição e manutenção.
Mesmo quando HSMs estão disponíveis para armazenar chaves, há sempre segredos para armazenar localmente, p. ex. o PIN do próprio HSM.
A primeira peça construída pela Prodist para a nova arquitetura multiplataforma é o cofre de segredos, denominado Prodist Vault.
O Prodist Vault de primeira geração está presente no STS desde o início para guardar senhas, inclusive os PINs de acesso a HSM e as senhas de arquivos PFX (a.k.a. PKCS #12). Sua implementação está fortemente amarrada ao Microsoft Windows.
O Prodist Vault de segunda geração armazenará registros nome/valor em um arquivo portável, multiplataforma. Cada registro terá seu sigilo e sua autenticidade assegurada por authenticated encryption with associated data (AEAD) com chave simétrica de 256 bits.
Cada cofre do Prodist Vault será por sua vez protegido por uma chave mestra fornecida por e sob controle da aplicação. A nova arquitetura de chave mestra permite que a aplicação use chaves armazenadas em arquivo, chaves acessadas via provedor CryptoKI (p. ex. HSM) e chaves armazenadas via provedor NCrypt (do Microsoft
Windows).
Serviço de chaves privadas
Serviços de chaves privadas se diferenciam de serviços de segredos em geral pelo objetivo de isolamento de chaves privadas, ou seja, de assegurar que as chaves privadas jamais serão copiadas para fora do seu perímetro de segurança.
Tais serviços devem operar com as chaves privadas em nome das aplicações, ou seja, devem fornecer uma interface com as operações de criptografia de que a aplicação necessita e um meio para que a aplicação faça uso dessas operações.
O Prodist STS original fornece operações via um protocolo proprietário que, por razões históricas, está fortemente amarrado aos conceitos e exigências do Sistema de Pagamentos Brasileiro.
O protocolo original é de difícil implementação e está disponível somente para linguagens / ambientes de programação DCOM (do Microsoft Windows) e Java.
O serviço original permite consultar e operar com chaves armazenadas no Prodist Vault de primeira geração ou com chaves acessadas via driver CryptoKI (p. ex. de um HSM).
O novo serviço de chaves privadas, que fará parte da nova arquitetura multiplataforma, fornecerá um novo protocolo proprietário, baseado em HTTP/2, projetado de antemão para cobrir uma ampla gama de aplicações, como p. ex. a assinatura digital de smart contracts Ethereum, sem perder capacidade nas aplicações atualmente
em produção.
O novo protocolo será maleável o suficiente para permitir módulos “cliente” em uma ampla gama de linguagens / ambientes de programação, incluindo C, C++, Java, C#, Python e outros.
O novo serviço permitirá consultar e operar com chaves armazenadas no Prodist Vault de segunda geração, com chaves acessadas via driver CryptoKI (p. ex. de um HSM) ou com chaves acessadas via provider NCrypt (do Microsoft Windows).
A Prodist visualiza arquiteturas com chaves privadas em cofres do Prodist Vault protegidos por chave mestra no chip TPM, garantindo um elevado nível de controle de acesso.
Serviço de certificados de chave pública
Certificados de chave pública, diferentemente de chaves privadas, são informações com o propósito expresso de serem divulgadas amplamente entre todos os participantes de uma rede, não exigindo sigilo nem na sua comunicação nem na sua armazenagem.
Serviços de certificado de chave pública são serviços especializados na consulta deste tipo específico de informação.
O Prodist STS original fornece operações via um protocolo proprietário que, por razões históricas, está fortemente amarrado aos conceitos e exigências do Sistema de Pagamentos Brasileiro.
O protocolo original é de difícil implementação e está disponível somente para linguagens / ambientes de programação DCOM (do Microsoft Windows) e Java.
O serviço original permite consultar certificados armazenados localmente, somente.
O novo serviço de certificados de chave pública, que fará parte da nova arquitetura multiplataforma, fornecerá um novo protocolo proprietário, baseado em HTTP/2, projetado de antemão para cobrir uma ampla gama de aplicações, como p. ex. a assinatura digital de aplicações (p. ex. Android ou iOS), sem perder capacidade nas
aplicações atualmente em produção.
O novo protocolo será maleável o suficiente para permitir módulos “cliente” em uma ampla gama de linguagens / ambientes de programação, incluindo C, C++, Java, C#, Python e outros.
O novo serviço, que fará parte da nova arquitetura multiplataforma, permitirá consultar certificados armazenados localmente ou acessados via driver ODBC / JDBC (p. ex. em banco de dados relacional).
A Prodist visualiza arquiteturas com certificados de chave pública em banco de dados, permitindo “ativação” atômica e distribuída durante procedimentos de renovação.
EXEMPLOS DE ARQUITETURA
Aplicação, um servidor de chaves & certificados e Prodist Vault
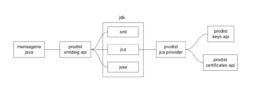
Neste exemplo, vamos descrever uma arquitetura com uma aplicação de mensageria trafegando mensagens XML assinadas, escrita em Java para rodar na JVM, integrada aos serviços de certificados de chave pública e chaves privadas, ambos executando em um único servidor, com dados armazenados localmente em um cofre do Prodist Vault.
No diagrama abaixo, representamos a montagem da aplicação. O módulo fictício Prodist xmldsig-api está na posição de algum dos módulos de domínio fornecidos pela Prodist, como por exemplo o Prodist pix-spi-api.
Este módulo fictício aplica a JDK para assinar mensagens XML e enviar estas mensagens para algum destinatário por um canal seguro TLS. Na JDK, os serviços de criptografia são fornecidos pela Java Cryptography Architecture, JCA, uma arquitetura baseada em provedores de serviço. O módulo Prodist jca-provider conecta a JCA aos serviços de chaves privadas e certificados de chave pública.
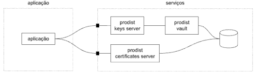
No diagrama abaixo, representamos a montagem da arquitetura, composta por dois “ambientes”, a aplicação, à esquerda, e os “serviços”, à direita, representando o fato de estarem isolados entre si. Chaves privadas e certificados de chave pública estão armazenados localmente no ambiente “serviços”, sendo que as chaves privadas são armazenadas em um cofre do Prodist Vault.
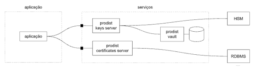
Aplicação, um servidor de chaves & certificados, HSM e RDBMS
Neste exemplo, descrevemos uma variação da arquitetura anterior, com as chaves privadas armazenadas em HSM e os certificados de chave pública armazenados em um banco de dados relacional. O ambiente de serviços ainda assim conta com um cofre do Prodist Vault para armazenar o PIN do HSM.
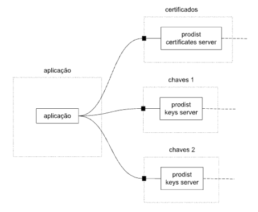
Aplicação, dois servidores de chaves, um servidor de certificados
Neste exemplo, descrevemos uma variação da arquitetura anterior, com o ambiente “serviços” separado em três ambientes independentes, “chaves 1”, “chaves 2” e “certificados”. Nesta arquitetura, as operações de criptografia são distribuídas com balanceamento de carga e tolerância a falhas. Omitimos as opções de armazenagem
anteriormente exemplificadas.